Smart contracts have become intricate to such an extent that the traditional auditing methods may prove insufficient in ensuring the security quotient. Though sectors such as healthcare, banking, governance, sports, and more handle sensitive data and critical processes, adopting smart contract auditing practices is paramount in the current scenario.
One real-life example that highlights the need for smart contract auditing is “The DAO Attack.” The DAO was a Blockchain-based venture capital fund built on the Ethereum platform that aims to create a decentralized organization where participants could invest and vote on projects using smart contracts.
In 2016, a vulnerability was exploited in the smart contract governing the DAO, resulting in a significant security breach. The attacker stole approximately one-third of the DAO’s funds, which amounted to millions of dollars. This cyber attack shook the crypto world that led to the Ethereum community conducting post-mortem analyses, code reviews, and subsequent hard forks to address the issue. This incident revealed the critical importance of smart contract auditing.
Those looking for authentic and well-researched resources to understand the importance of smart contract auditing in addition to smart contract audit cost, smart contract auditing process, top smart contract audit firms, and more factors surrounding the concept have come to the right place.
This comprehensive guide sheds light on the following prominent aspects surrounding smart contract auditing:
- Most Common Smart Contract Security Vulnerabilities
- Prominent Smart Contract Auditing Practices to Eliminate Security Vulnerabilities
- Perks of Leveraging Smart Contract Auditing Services
- Smart Contract Auditing Process: Key Steps to Follow
- Primary Factors to Choose the Best Smart Contract Audit Company
- How to estimate the Smart Contract Audit Cost?
- Top Smart Contract Security Auditors
- Conclusion
Most Common Smart Contract Security Vulnerabilities
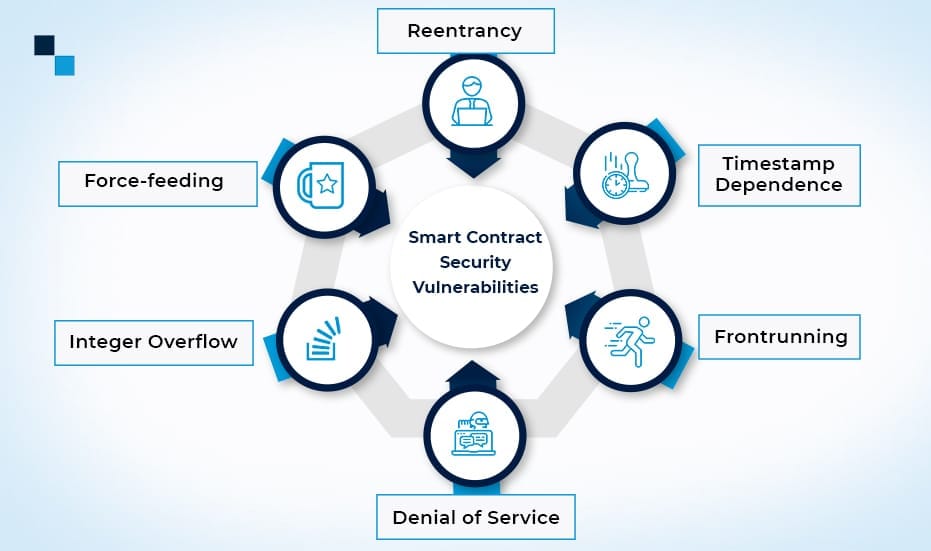
Reentrancy
Reentrancy is a vulnerability that occurs when a malicious actor uses a “reentrancy bug” to call a function repeatedly in the smart contract before the existing program’s execution. An attacker can repeatedly call back into the vulnerable contract, executing malicious code and potentially manipulating the contract’s state or funds.
Reentrancy could be mitigated by implementing the “Checks-Effects-Interactions” pattern, where all external contract calls are placed after modifying the contract’s state. In addition to that, the “withdraw pattern” could also be used for handling Ether transfers, ensuring that the contract’s balance is updated before sending funds to external accounts.
Timestamp Dependence
Timestamp dependence is one of the most common smart contract security vulnerabilities that appears when “block.timestamp” function is used to execute critical logic. Exploiting timestamp dependence, a hacker can manipulate the timestamp to trick the contract into behaving in an unintended manner.
One of the best ways to overcome smart contract security vulnerabilities like timestamp dependence is to use block number or block hash instead of relying solely on the timestamp for critical decision-making. Consider implementing mechanisms such as block confirmation to ensure that a certain number of blocks have passed since the timestamp before taking any actions.
Frontrunning
Frontrunning typically involves an attacker monitoring pending transactions and executing a transaction with a higher gas price to override or manipulate the desired outcome of a targeted transaction. Such attacks occur mostly on public Blockchain platforms like Ethereum. Crypto miners use frontrunning to earn profits during trading.
The impact of Frontrunning attack could be minimized by carefully analyzing the gas price and transaction order. Developers can also employ techniques such as the use of commit-reveal schemes, where sensitive information is revealed after the transaction is confirmed.
Denial of Service (DoS)
Attackers exploit DoS vulnerability by consuming excessive gas, triggering infinite loops, or causing other resource-intensive operations that deplete the contract’s resources. bid() function and fallback() functions are used by attackers to make the DoS attack possible.
To mitigate DoS vulnerability, developers must carefully analyze the contract’s logic and ensure that critical operations have predefined limits, such as gas limits or iteration bounds, to prevent resource exhaustion.
Integer Overflow
When the result of an arithmetic operation exceeds the maximum value represented by the variable type, then the smart contract vulnerability called integer overflow occurrs. Some drastic outcomes of this vulnerability include unexpected behavior, erroneous calculations, and potential security risks.
Developers could reduce the possibilities of integer overflow with the usage of safe arithmetic libraries or data types that automatically check for overflow conditions. Defensive programming techniques, such as bound validations and range checks could also be used to overcome this vulnerability.
Force-feeding
Force-feeding, also known as transaction-ordering dependence, is a smart contract vulnerability that arises when the outcome of a contract’s execution depends on the order in which transactions are included in a block. Attackers forcibly transfer Ether to smart contracts to manipulate balance checks.
To overcome force-feeding vulnerabilities, developers should design contracts with a focus on transaction atomicity, ensuring that the contract’s logic and outcomes are independent of the order in which transactions are executed. Implementing mechanisms such as commit-reveal schemes, where sensitive data is revealed after transactions are confirmed, can help protect against force-feeding attacks.
Prominent Smart Contract Auditing Practices to Eliminate Security Vulnerabilities
A smart contract audit company could adopt either manual auditing or automatic smart contract auditing practices or both to execute a complete audit operation.
1. Manual Auditing
Performing a manual audit involves auditors detecting hidden errors and design issues by manually reviewing the contract’s code. The following are some manual auditing techniques followed by smart contract audit firms:
- Documentation Analysis
Auditors review the entire document along with details like architectural requirements and product design. It helps auditors understand asset flow, program constraints, threat models, the interaction between contracts, risk mitigation measures, and more.
- Specification Analysis
Auditors create a detailed project document to outline product specifications and showcase the functional design. Any shortcomings or assumptions made during the development and design of the project could be easily identified by performing specification analysis.
2. Automated Auditing
Automated auditing is performed using smart contract auditing tools to generate rapid results. These tools can help identify coding errors and common security vulnerabilities such as the reentrancy attack, coding errors, integer overflow/underflow, unchecked external calls, and more. Here are some auditing techniques that fall under automated auditing:
- Fuzzing
The process of testing contracts automatically by integrating them with random and unexpected outputs is known as Fuzzing. From memory leaks to crashes to failed built-in code insertions, fuzzing is used to identify multiple smart contract vulnerabilities.
- Testing
Smart contract testing is a bit similar to software development testing performed to check if the application behaves as intended. It helps auditors provide several edge cases for vulnerability assessments and indicate the project’s maturity.
- Static Analysis
It is a combination of control flow and data flow analysis. From return statements to infinite loops, control flow analysis is performed to inspect control flow through the entire program. On the other hand, data flow analysis determines how data is stored, used, and reorganized throughout the program.

Perks of Leveraging Smart Contract Auditing Services
Enhanced Security Quotient
Smart contract auditing helps identify weaknesses and vulnerabilities in the contract’s code. Potential security risks such as hacking, unauthorized access, and fund loss can be mitigated. Auditing practices ensure that the contract is built with robust security measures, protecting the assets and interests of both users and project stakeholders.
Compliance and Regulation
Smart contract auditing can ensure compliance with legal and regulatory requirements. Auditing practices help verify that the contract adheres to applicable laws, industry standards, and governance frameworks. It is imperative for businesses to perform a smart contract audit for projects, operating in regulated sectors such as healthcare or finance, where compliance is a crucial factor.
Financial Loss Control
Smart contract auditing helps prevent potential financial losses caused by flaws or vulnerabilities in the contract’s code. Adopting smart contract auditing practices reduce the chances of funds being stolen, contracts being exploited, or unintended behaviors impacting user transactions.
Early Error Detection
Smart contract auditing practices allow for early detection and resolution of issues before the contract is deployed. By conducting audits during the development phase, potential vulnerabilities can be identified and fixed before they pose a risk to the project. Early detection reduces the cost and effort of fixing issues in later stages and minimizes the impact on users and stakeholders.
Better Code Quality
Auditing practices focus on code review and analysis, which improves the overall quality of the smart contract’s codebase. Auditors provide valuable insights and recommendations for code optimization, adherence to best practices, and improved readability. This leads to more maintainable and efficient code, reducing the likelihood of future bugs or vulnerabilities.
Smart Contract Auditing Process: Key Steps to Follow
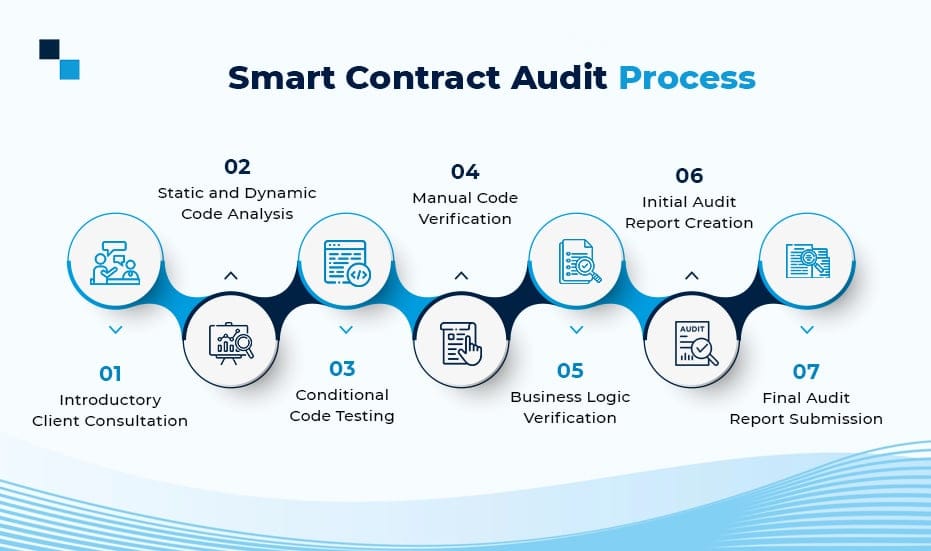
1. Introductory Client Consultation
The security auditors discuss functional requirements and analyze code design patterns with the client. The auditor also works closely with the project team to understand the objectives, specifications, and requirements of the project. This step helps in establishing a clear understanding of the contract’s purpose and functionality.
2. Static and Dynamic Code Analysis
The auditor performs a thorough review of the smart contract’s source code with automated tools to identify compilation issues, malicious code, and potential errors. It involves analyzing the code structure, logic, and implementation details. The code analysis can also focus on best coding practices, efficiency, and readability.
3. Conditional Code Testing
Auditors perform conditional code testing to deploy smart contracts on a local sandbox environment and prevent unnecessary gas consumption by verifying the gas limits.
4. Manual Code Verification
Manual code verification includes reviewing the contract for common vulnerabilities such as overflow, underflow, reentrancy, timestamp dependence, and other known security risks.
5. Business Logic Verification
The auditor tests the smart contract’s functionality against the defined requirements to confirm whether the project is architectured as per the business logic. This involves executing different scenarios, inputs, and edge cases to verify that the contract functions correctly and produces the expected results.
6. Initial Audit Report Creation
The initial audit report highlights the number of risks encountered during the audit process. It may also include suggestions for optimizing code, enhancing security measures, or improving overall contract quality.
7. Final Audit Report Submission
The final report will be delivered along with vulnerability details, recorded risks, and areas that require attention.
Primary Factors to Choose the Best Smart Contract Audit Company
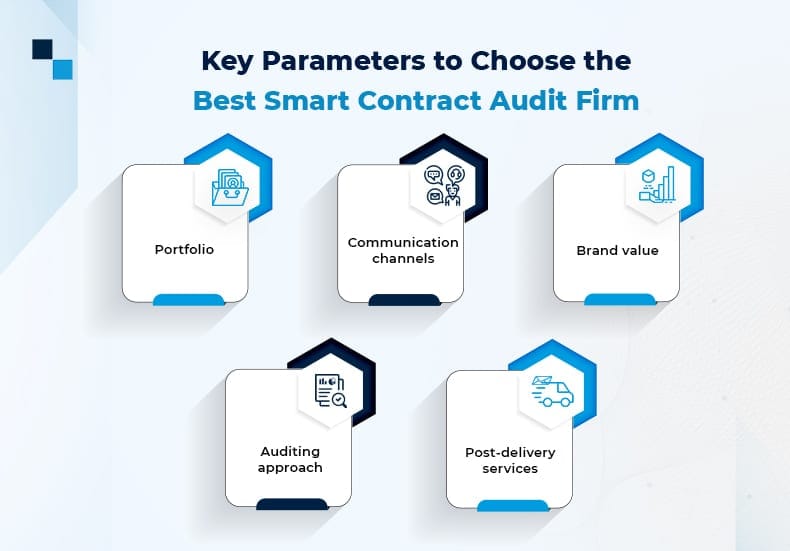
Portfolio
Look for firms with a track record of successful audits, experienced auditors, and a deep understanding of Blockchain technologies, security best practices, and relevant programming languages. The portfolio of a smart contract audit firm will help you understand coding standards and practices being followed by the team.
Communication Channels
Prefer to hire a smart contract audit firm that maintains clear and open communication throughout the auditing process. Effective communication ensures a smooth collaboration, allows for timely feedback and clarifications, and helps you understand the audit findings and recommendations.
Brand Value
Factors such as ratings & reviews, social networking portals, client testimonials, and search engine rankings will help you gauge online brand reputation of a smart contract audit company. Frim’s ratings on Clutch, GoodFirms, AppFutura, and more can also help you to measure the online brand value of an organization.
Auditing Approach
Evaluate the firm’s auditing methodologies and tools. Ensure they employ a combination of advanced automated analysis tools and manual code reviews to thoroughly assess the functionality and security of smart contracts. It is recommended to choose one that follows an iterative and collaborative approach while smart contract development, deployment, and auditing.
Post-delivery services
Evaluate whether the firm offers additional services, such as code review, security consultation, or support during the remediation process. These additional services can add value and streamline overall security efforts.
How to Estimate the Smart Contract Audit Cost?
Project Size
The size of your Blockchain project is one of the deciding factors to estimate the smart contract audit cost. Complex contracts with intricate logic, multiple functionalities, or extensive interactions with external systems may require more time and effort to review. Moreover, the size of the smart contract’s codebase, including the number of lines of code, can impact the audit cost. Larger contracts typically require more time to analyze and verify, leading to higher costs.
Blockchain Platform
The price of an audit also varies from platform to platform. For instance, the estimated cost for performing an Ethereum smart contract development and audit depends on Ethereum’s gas fees, storage fees, contract execution process, and many more factors. On a similar note, the smart contract audit cost for Blockchain platforms like Tron, Solana, Polkadot, and more may depend on their features and architecture.
Firm’s Expertise
The reputation, experience, and expertise of the auditing firm or individual can impact the cost. Highly regarded auditors with a proven track record of smart contract audits may command higher fees. Moreover, factors such as tools and technologies required to audit an application, maintenance & post-delivery services, and project management cost also contribute to the smart contract audit cost.
Audit Process
The smart contract audit process followed by a smart contract audit company may also affect the audit cost. From code assessment to expert review to creating detailed audit reports, there are countless steps involved in the detailed smart contract audit process. The strategy and process being followed may also differ from one smart contract audit company to another.
Top Smart Contract Security Auditors

Antier
Antier is a trusted smart contract audit firm dedicated to ensuring the security, reliability, and robustness of blockchain-based projects. Antier’s auditors meticulously examine smart contract code, reviewing every aspect to uncover potential security loopholes, bugs, or vulnerabilities. They employ a combination of manual code analysis and advanced automated tools to conduct a thorough security assessment. From analyzing the contract’s logic and architecture to scrutinizing external dependencies and integration points, Antier’s auditing process leaves no stone unturned. The company has successfully audited a wide range of projects, including decentralized finance (DeFi) platforms, non-fungible token (NFT) marketplaces, and blockchain-based applications.
CertiK
CertiK is a leading smart contract audit firm specializing in smart contract security. With their team of seasoned experts and cutting-edge technology, CertiK is dedicated to providing comprehensive and reliable audits to ensure the integrity, safety, and functionality of decentralized applications and smart contracts. CertiK applies rigorous testing methodologies to deliver accurate and in-depth security assessments. With a reputation for professionalism and reliability, the company has earned the trust of numerous clients, including prominent Blockchain projects, financial institutions, and enterprises.
MythX
MythX is a renowned smart contract audit company specializing in smart contract security and analysis. As a leader in the field, MythX leverages cutting-edge techniques such as symbolic execution, static analysis, and fuzzing to thoroughly analyze smart contracts for potential security risks. By combining automated analysis with manual reviews, the company delivers accurate and actionable reports, highlighting identified issues and providing recommended solutions. MythX’s reputation for excellence in smart contract auditing has made them a trusted partner for blockchain startups, enterprises, and decentralized application (dApp) developers.
Quantstamp
Quantstamp’s approach to auditing combines manual reviews with advanced automated tools to identify potential vulnerabilities and security risks in smart contracts. What sets Quantstamp apart is its focus on innovation and scalability. Their comprehensive audits, backed by cutting-edge technology and industry expertise, enable projects to enhance their security posture, mitigate risks, and maintain the highest standards of quality and trustworthiness in the Blockchain ecosystem.

Conclusion
There is no denying that the future potential of smart contract audit is immense, driven by the growing complexity of decentralized applications. As Blockchain technology finds applications in sectors beyond cryptocurrencies, such as supply chain management, healthcare, and governance, the importance of smart contract audit will surely intensify in the foreseeable future.
Additionally, the emergence of artificial intelligence (AI) and machine learning (ML) technologies can enhance smart contract auditing capabilities. AI-based algorithms can assist auditors in analyzing large amounts of code, detecting patterns, and identifying potential vulnerabilities more efficiently. ML models can learn from historical audits and security incidents to improve the effectiveness and accuracy of future audits.
Smart contract auditing will play a vital role in fostering trust, protecting users, and facilitating the mainstream adoption of Blockchain solutions across various industries.





