Let’s face it, cybercriminals didn’t take a break during last year’s summer. According to a report shared by Statista in April 2023, approximately 72 percent of global businesses indicated that their organization was at risk of cyber attacks. As more individuals venture into the online sphere, the potential for cyber criminals to exploit vulnerabilities is likely to grow in the future.
Another report by Statista reveals that the global cost of cybercrime is expected to surge from $9.22 trillion in 2024 to $13.82 trillion by 2028. Such statistics make a very sound case for businesses to double down their investments in data security strategies surrounding zero-knowledge architecture. This blog post serves as a beginner’s guide for B2B professionals looking to get detailed information about zero-knowledge encryption and covers the following aspects:
Table of Contents
- What is Zero-Knowledge Encryption?
- Zero-Knowledge Encryption vs End-to-End Encryption: The Difference
- Prominent Benefits of ZK Encryption for B2B Collaboration
- Real-World Applications of Zero-Knowledge Encryption
- Platforms Utilizing Zero-Knowledge Encryption
- How ZK Encryption is Reinventing Blockchain Privacy?
- The Road Ahead
What is Zero-Knowledge Encryption?
Zero-knowledge encryption is a cutting-edge cryptographic technique designed to enhance data security and privacy. Unlike traditional encryption methods where data is encrypted and decrypted using keys that are known to both the sender and the recipient, zero-knowledge encryption operates on a different principle. Here’s what sets it apart:
- Client-side encryption: Data is encrypted on your end using a private key before being sent to a server or shared with another party.
- Zero-knowledge proof: Recipients can verify the possession of data without ever seeing it in its decrypted form. ZK encryption uses complex cryptography to prove ownership without revealing the actual data.
- No central key repository: There’s no single point of failure – even the service provider facilitating the exchange cannot decrypt the data without your private key.
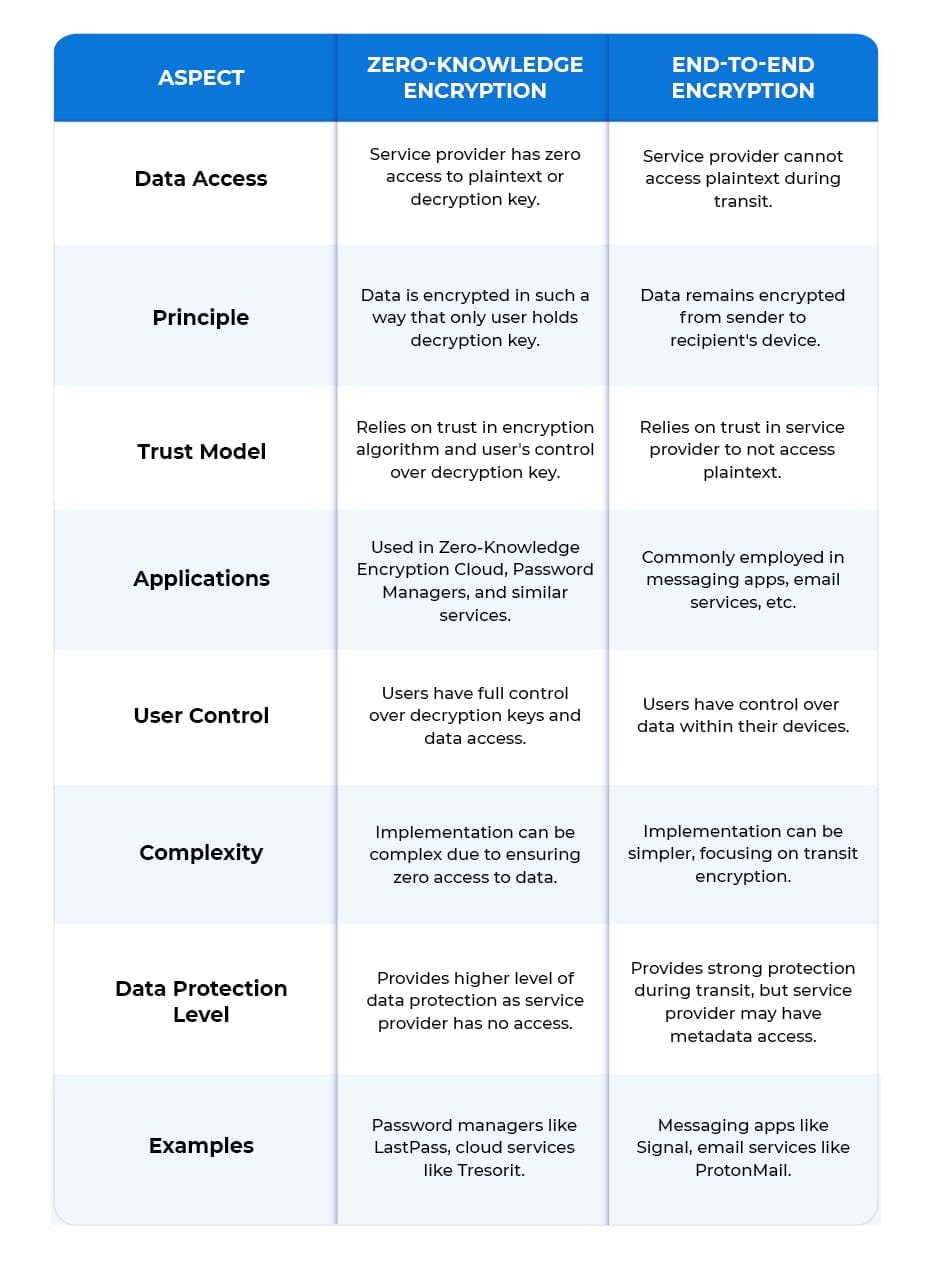
Zero-Knowledge Encryption vs End-to-End Encryption: The Difference
While both zero-knowledge encryption and end-to-end encryption aim to safeguard data privacy, they differ in their approach.
Prominent Benefits of ZK Encryption for B2B Collaboration
In today’s hyper-connected business world, collaboration is key. However, sharing sensitive data with partners, vendors, and suppliers can be a security nightmare. Investing in zero-knowledge encryption can empower your organization to:
Enhance Compliance with Regulations
Data privacy regulations like GDPR and CCPA are becoming increasingly stringent. ZK encryption can be a valuable tool for demonstrating compliance:
- Strong data security: ZK encryption focus on user control and limited access aligns perfectly with the “right to be forgotten” and other privacy principles enshrined in these regulations.
- Improved audit trails: Comprehensive audit logs can be maintained without compromising data confidentiality. This allows for easier demonstration of compliance efforts to regulatory bodies.
Foster Trust and Transparency in Partnerships
Building trust with partners is crucial for successful B2B collaboration. ZK encryption facilitates this by:
- Secure data sharing: Businesses can confidently share sensitive information with partners without compromising confidentiality. This fosters a more open and collaborative environment.
- Demonstrated commitment to data privacy: By adopting ZK encryption, companies signal their dedication to responsible data stewardship, boosting trust and reputation among partners.
Streamline Workflows and Boost Efficiency
Traditional encryption methods can create friction in workflows. ZK encryption helps streamline data exchange.
- Simplified data sharing: Eliminate the need for manual decryption and re-encryption, allowing for seamless data transfer between authorized parties.
- Reduced administrative burden: ZK encryption eliminates the need to manage and distribute encryption keys centrally, streamlining administration and minimizing human error.
Unlock the Potential of Emerging Technologies
ZK encryption is at the forefront of innovative technologies like blockchain and secure multi-party computation.
- Secure data exchange in blockchains: It enables secure and verifiable data sharing on blockchain platforms without compromising privacy.
- Enhanced privacy in multi-party computation: It allows multiple parties to analyze data collaboratively without revealing sensitive details, facilitating secure data insights.

Real-World Applications of Zero-Knowledge Encryption
- Enhanced Supply Chain Visibility
Ensuring ethical sourcing and regulatory compliance throughout complex supply chains can be challenging. ZK encryption allows participants to share sensitive data without revealing specifics. This fosters transparency and simplifies compliance audits.
- Verifiable Voting in Consortiums
Traditional voting within B2B consortiums can be vulnerable to manipulation or lack of transparency. ZK encryption allows members to verify their eligibility to vote without revealing their identity or vote choice. This ensures a secure and verifiable voting process within industry associations or governing bodies.
- Protecting Intellectual Property
Zero-Knowledge encryption provides a robust defense against IP theft and unauthorized access by encrypting proprietary documents, research findings, and product designs. With ZK encryption, businesses can share valuable intellectual property with collaborators, partners, and stakeholders while maintaining control over who can access and view the information, thus preserving its integrity and confidentiality.
- Secure Cloud Storage
Cloud storage offers scalability and convenience, but concerns linger about data privacy when it resides on a third-party server. ZK encryption allows you to encrypt data client-side before uploading it to the cloud. Partners can verify access rights without ever decrypting the data, ensuring confidentiality while leveraging cloud storage benefits.
Platforms Utilizing Zero-Knowledge Encryption
1. Tresorit

A pioneer in secure cloud storage, Tresorit provides businesses with a Zero-Knowledge encryption platform to store and share sensitive files. What sets Tresorit apart is its commitment to data privacy, ensuring that files are encrypted before they leave the user’s device and remain inaccessible to anyone else, including Tresorit’s own servers. This level of security is crucial for industries dealing with confidential data, such as legal firms, healthcare organizations, and financial services.
2. Signal

While primarily known as a secure messaging app for individuals, Signal’s protocol also serves as the backbone for secure business communication that requires absolute privacy. With end-to-end encryption and a zero-knowledge policy, Signal ensures that messages, calls, and files are visible only to the sender and the recipient, making it a trusted platform for sensitive business communications.
3. LastPass

Among the most popular zero-knowledge password managers, LastPass allows users to store passwords and other sensitive information in a secure vault. The master password, which decrypts the vault, is never shared with LastPass, embodying the zero-knowledge principle. For businesses, this means enhancing security without sacrificing convenience, as employees can securely access shared accounts without exposing credentials.
4. Ledger

In the realm of cryptocurrency, securing one’s private keys is paramount. Ledger’s hardware wallets offer a zero-knowledge security feature, ensuring that the user’s private keys never leave the device and are not accessible to anyone, not even Ledger. This level of security is crucial for businesses and individuals dealing with cryptocurrencies, providing peace of mind that funds are safe from unauthorized access.
How ZK Encryption is Reinventing Blockchain Privacy?
Blockchain technology is celebrated for its transparency, immutability, and security. However, this transparency often comes at the cost of privacy, with every transaction recorded and visible on the public ledger. ZK encryption can mitigate this issue by allowing transactions to be verified without revealing the sender, receiver, or transaction amount. This not only enhances privacy but also opens up new avenues for blockchain applications in sectors where confidentiality is paramount, such as finance, healthcare, and identity management.
For example: Zcash
One of the most notable implementations of zero knowledge encryption in the blockchain space is Zcash, a cryptocurrency designed to offer enhanced privacy for its users. Zcash utilizes zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) to enable transactions without disclosing the payment’s sender, receiver, or amount. This level of privacy ensures that Zcash transactions are fully encrypted on the blockchain, providing users with the option for enhanced anonymity.

The Road Ahead
Zero-knowledge encryption is no longer just a futuristic concept. It’s a powerful tool that can transform how B2B organizations collaborate securely. The integration of zero-knowledge encryption into blockchain technology holds immense potential for the future of digital transactions. By enabling secure and private transactions, ZK encryption can help overcome one of the major hurdles facing blockchain adoption in various sectors. Additionally, ZK encryption can be integrated with AI algorithms, allowing for training on sensitive data without compromising privacy. Those willing to know more about the concept of ZK encryption must get in touch with experts at Antier.