
Your Roadmap from IDO Launchpad to a Thriving DEX Aggregator in 2025 and Beyond
April 8, 2025
Why White Label Gaming Solutions Are the Future of Game Development?
April 8, 2025Introduction
Data privacy in today’s web3 era has become both a necessity and a challenge. From online banking to enterprise communication systems, protecting sensitive information without compromising performance is a constant balancing act. Transport Layer Security (TLS), the protocol behind HTTPS, has long been the backbone of secure communication. However, the TLS protocol also has its limitations. While TLS encrypts data in transit, it does not guarantee complete privacy.
This is where the zkTLS protocol steps in. It’s a cutting-edge solution designed to enhance network privacy without sacrificing speed or scalability. This protocol is an amalgamation of Zero Knowledge Proofs (ZKPs) and the TLS protocol, which opens the door to verifiable yet private communication, ideal for industries where confidentiality is of the utmost critical.
In this blog, we’ll break down what the zkTLS protocol is, how it works, and explore key zkTLS use cases across various industries.
What is TLS?
Whenever you see the padlock symbol in your browser’s address bar or visit a website that starts with “https://”, it shows you are using the TLS protocol.
Transport Layer Security (TLS) is a cryptographic protocol that boosts data privacy, integrity, and authenticity between two communicating parties, i.e., a client and a server.
TLS operates through a handshake mechanism where the client and server agree on cryptographic parameters before exchanging encrypted data. The handshake involves exchanging certificates, verifying identities, and generating session keys.
With 95% of internet activity secured by TLS, this mechanism has worked well for decades. However, the TLS protocol does not inherently support proof of communication without revealing content, which is a basic requirement in privacy-focused decentralized networks.
TLS has its limitations-
- It reveals metadata like handshake transcripts.
- It requires trust in certificate authorities.
- It can expose session information if either end is compromised.
In sensitive industries like finance, healthcare, or blockchain-based systems, where data leakage, even metadata, can be catastrophic, there’s a growing need for something more private and efficient. This is where zkTLS steps in. First, let’s skim through what zk proofs are.
What are Zero-Knowledge Proofs?
Zero Knowledge Proofs (ZKP) are cryptographic methods where one party (the prover) can prove to another party (the verifier) that a statement is true without revealing any information beyond the validity of the statement itself.
There are three essential properties of ZKPs:
- Completeness: If the statement is true, the verifier will be convinced.
- Soundness: If the statement is false, no dishonest prover can convince the verifier.
- Zero-Knowledge: No information about the statement itself is revealed.
In recent years, zk proofs have gained significant attention in blockchain networks like Zcash (the first real-world application of zero-knowledge proofs) for enhancing privacy without sacrificing transparency.
zkTLS – Combining zk Proofs and TLS for Next-Gen Network Security
zkTLS represents the integration of Zero Knowledge Proofs with the TLS protocol. Zero-Knowledge Transport Layer Security or zkTLS creates a protocol that facilitates safe data transmission with the added benefit of a verifiable privacy layer on top.
zkTLS is a hybrid model that enables clients and servers to prove a TLS session has occurred, without revealing any actual session data or TLS transcript.

Instead of modifying TLS itself, zkTLS typically wraps around a TLS handshake and generates a zero-knowledge proof that the handshake followed the TLS protocol correctly. Third parties (e.g., smart contracts, blockchain validators) can verify that the handshake was done correctly without seeing the actual exchanged data. This allows decentralized systems or on-chain applications to trust that the TLS communication was secure while still preserving privacy.
zkTLS proofs are especially useful in bridging Web2 and Web3 and allowing decentralized systems to verify secure communication with centralized services without relying on blind trust.
Why We Need zkTLS
The internet was originally designed to be open, flexible, and user-centric. Early Web2 platforms like Twitter, Facebook, Uber, and LinkedIn supported this vision and provided open APIs that enabled developers and users to create and connect applications. This approach promoted innovation and interoperability.
However, as these platforms grew and gained market dominance, their priorities shifted from openness to control. Instead of allowing easy data sharing, they started restricting access to protect their user data and maximize profits. They created closed ecosystems, also known as walled gardens, where user data is locked inside a platform, hence, limited portability and external use.
The main reason behind this data control lies in the security framework of the internet. Today, most online communication is protected by Transport Layer Security (TLS), which secures connections between users and websites. However, TLS has a flaw. It monopolizes user data visibility, meaning only platforms can verify and control the data.
How zkTLS Solves This Problem
Zero-Knowledge Transport Layer Security or zkTLS is designed to break this data monopoly. It enables third parties to verify user data without relying on the platform and exposing sensitive information. This is achieved through zk proofs, a cryptographic technique that ensures privacy.
With zkTLS:
- User data can be verified without needing platform approval.
- User data becomes portable, meaning users can prove information across different applications and services.
How does zkTLS Work
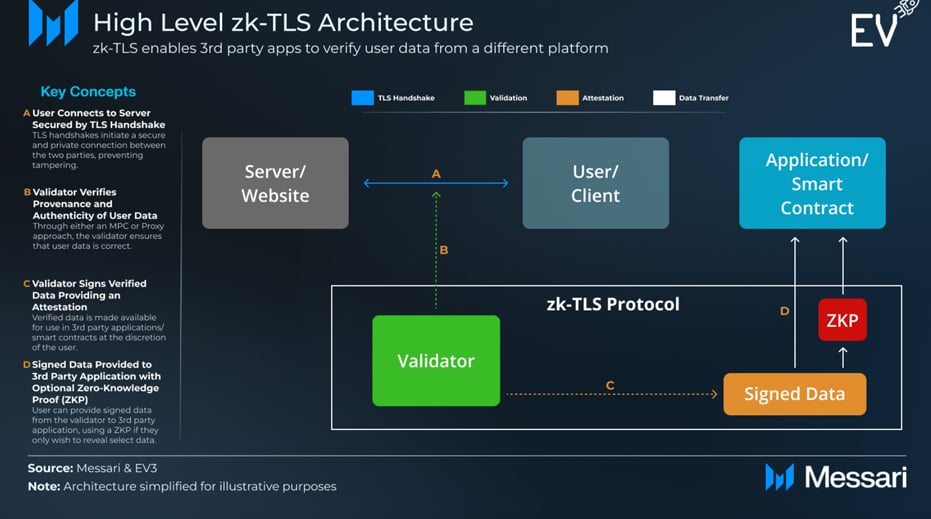
zkTLS Architecture
The technical implementation of zkTLS can be broken down into three broad approaches–
- Multi-Party Computation (MPC) schemes like Opacity and Primus,
- Proxy-based approaches like Reclaim and Pluto, and
- Trusted Execution Environment (TEE) based architecture like Clique.
Remember this- the goal of zkTLS proofs is to verify that a user logged in correctly and the server returned the appropriate information.
1. MPC Architecture
In the MPC (Multi-Party Computation) approach, a trusted node, called a notary, helps the user log in securely. The key idea behind MPC is that multiple parties can conduct computation. No single party can control or manipulate the system.
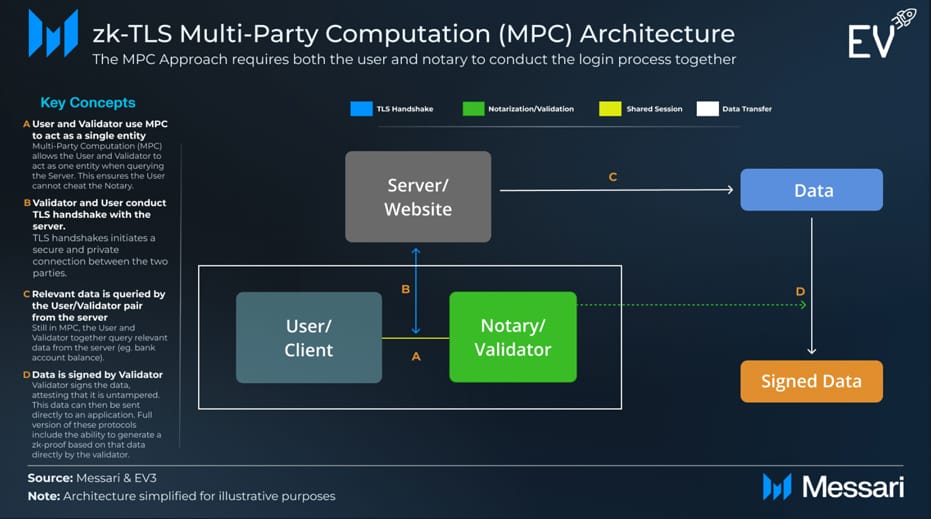
zkTLS Multi-Party Computation (MPC) Architecture
Think of the MPC approach like a door with two locks, where Alice has one key and Bob has the other. The door only opens when both are present with their keys. In the same way, the notary and the user must work together correctly; otherwise, the notary won’t approve the login, and access will stay locked.
2. Proxy Architecture
The proxy approach in zkTLS leverages web browsers’ proxy features. Instead of sending messages directly to the website’s server, the browser sends them through a validator node acting as an HTTPS proxy. This node sees encrypted messages from both the server and client but cannot decrypt them. Instead, it signs messages to verify their origin. The client, in-browser, then generates a zero-knowledge proof that confirms the correct information corresponding to the encrypted data was accessed and also fits specific criteria without revealing the actual data.
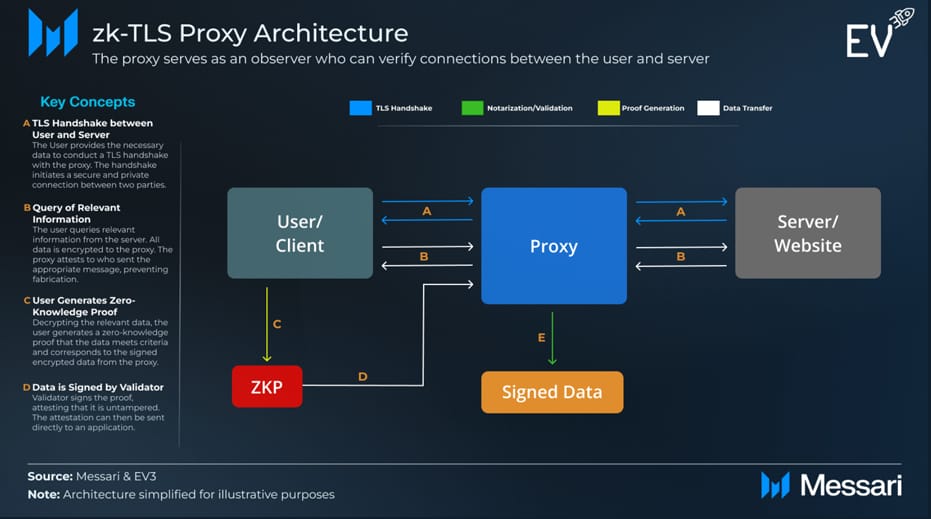
zkTLS Proxy Architecture
However, this method faces scalability issues. If a bank server, like JP Morgan’s, detects excessive requests from a single proxy, it may block them. Using residential IP proxies can be a solution to mitigate this issue, but it introduces reliability concerns and security risks. Attackers could manipulate residential IP proxies to generate fraudulent proofs.
3. Trusted Execution Environment (TEE)
A simple way to use zkTLS is through Trusted Execution Environments or TEEs. These are secure areas within a device’s processor that offer an isolated environment for data processing or code execution.
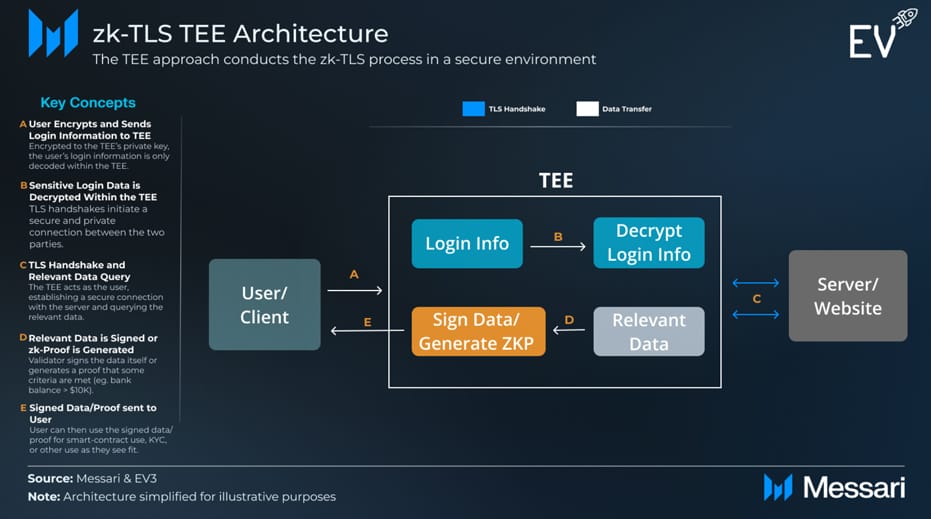
zkTLS TEE Architecture
When a user logs in, their credentials (like a password) are encrypted and sent to the TEE. The TEE then decrypts this information securely, which acts as the user to handle the TLS handshake. It communicates with the server on the user’s behalf, while ensuring that no sensitive data is exposed, even to the device’s owner.
After processing, the TEE can either return the signed data or generate a zero-knowledge proof, a way to confirm that the data meets certain conditions without revealing what it actually is. This architecture ensures web3 security and privacy.
Explore the zkTLS Use Cases
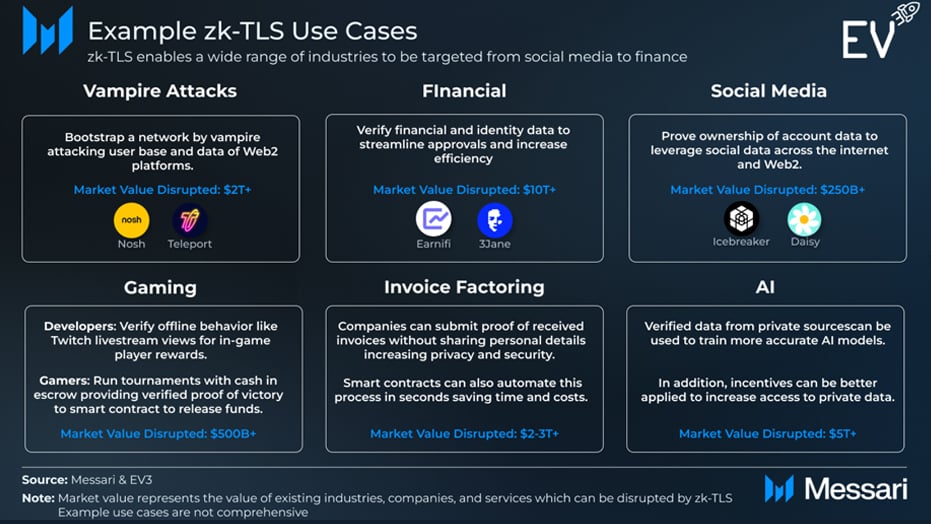
1. Web2 Vampire Attack
DePIN platforms like Nosh (food delivery) and Teleport (ridesharing) utilize the zkTLS protocol to onboard gig workers from Web2 platforms while maintaining quality standards. This approach enables DePIN-based platforms to reduce fees, increase earnings, and challenge centralized intermediaries like Uber that take a significant cut of user fees. Such a strategy helps build a more equitable model for workers while ensuring verified driver data without compromising privacy.
2. Financial
zkTLS enables financial institutions to verify transaction authenticity, customer credentials, and compliance with regulations while preserving confidentiality. In cross-border payments, zkTLS minimizes data exposure, which reduces fraud risks and meets privacy regulations. It also enables transparent yet private interactions between users and smart contracts that help secure decentralized finance (DeFi) platforms. As the transaction details remain hidden while proving validity, zkTLS is ideal for secure banking, payment processing, and regulatory compliance in the financial sector.
3. Social Media
zkTLS enables verifiable, privacy-preserving influencer collaboration that revolutionizes the whole concept of social media monetization. Platforms like Daisy utilize zkTLS to confirm influencer interactions, such as likes, shares, or comments, without revealing personal data. This verification fosters multi-influencer campaigns, improves engagement, reduces ad spend, and enhances content virality across overlapping social media networks.
4. Gaming
In the entertainment and gaming sector, zkTLS enables decentralized, trustless tournament models. Players can escrow funds in smart contracts and withdraw winnings only after proving victory through zkTLS. It also facilitates player incentives like special in-game rewards for streaming participation, ensuring consent-based proof of activity without compromising user privacy.
5. Invoice Factoring
Large corporations like Coca-Cola rely on regional trucking firms for deliveries, but impose 30–60 day payment terms. To sustain operations, trucking companies use invoice factoring, a $3 trillion market in 2020, projected to hit $5 trillion by 2026. However, verifying invoices is manual and insecure, often requiring login credential sharing. zkTLS solves this by allowing such trucking firms to prove invoice validity without exposing sensitive data. Initially, underwriters confirm proofs, but as financial institutions adopt on-chain flexibility, smart contracts could automate the process. This enables trucking firms to receive payments within minutes, which enhances security and efficiency without human oversight.
6. AI
zkTLS offers a solution to the AI industry’s data shortage. It allows small AI model developers to access and verify high-quality, domain-specific data from private sources without risking privacy. This enables competitive model training at lower costs. Additionally, zkTLS supports intent-based agent networks by verifying off-chain actions securely and efficiently.

Conclusion
The digital world is shifting towards a future where privacy and performance are non-negotiable. Traditional protocols like TLS, while effective, fall short of providing complete confidentiality. The integration of zk proofs into TLS, resulting in zkTLS, marks a paradigm shift in how we think about secure communication.
zkTLS protocol bridges the gap between privacy and efficiency in modern networks. Businesses, blockchain networks, healthcare providers, and financial institutions looking to future-proof their communication systems should start exploring zkTLS integration now. And in this case, we at Antier can help you.
At Antier, we specialize in cutting-edge zero-knowledge cryptography solutions, helping organizations seamlessly integrate zkTLS into their existing infrastructure. With our expertise, businesses can fortify their communication networks, enhance data privacy, and stay ahead in an increasingly web3 security-conscious world.
The future of secure communication isn’t just encrypted. It’s private, provable, and performance-driven, and with Antier’s zkTLS integration support, you can lead the charge.



