Today’s technology-driven world offers instant conveniences but at a cost, i.e., our privacy. With a few clicks, we share sensitive data – location, transaction history, and more – exposing ourselves to identity theft and fraud. This isn’t unique to the digital world; even blockchains, known for transparency, face privacy challenges. Several smart contract use cases require confidentiality for legal or business reasons. To address this need for privacy on public blockchain networks, zero-knowledge proofs (primarily used by ZK-rollups) emerge as a formidable solution.
Zero-knowledge-proof technologies, such as ZK-STARKs and ZK-SNARKs, play a vital role in bringing privacy to blockchain. This blog will delve into zero-knowledge proof and the detailed comparison of ZK-STARKs vs ZK-SNARKs.
What is Zero Knowledge Proof?
A zero-knowledge proof is a mechanism that enables one party (the prover) to validate the statement to another party (the verifier) that it is true without revealing the statement itself. The ‘prover’ is the party trying to prove a claim, whereas the ‘verifier’ is the one who validates the claim.
Several advancements have been made in zero-knowledge proofs over the years and they are now being used for various purposes, such as authentication, anonymous payments, identity protection, verifiable computation, and more.
Key Benefits of Zero-Knowledge Proofs
- Privacy: ZKPs allow the prover to prove to the verifier that a statement is true without revealing any additional information. It ensures the privacy of sensitive data.
- Scalability: A block that requires ages to verify can simply be done by a single person. They can do the computation and produce proofs like ZK-STARKs while other network participants simply validate the provided proof.
- Simplicity: ZKPs don’t require any technical knowledge to operate and this is one of the most noted attributes users appreciate about it.
Understanding ZK-SNARKs & ZK-STARKs
ZK-SNARK and ZK-STARK are the two most powerful cryptographic techniques in the market today that are used to provide zero-knowledge proofs. Here’s an explanation of each
ZK-SNARK
ZK-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) is a cryptographic proof that enables one party to validate certain information without performing lengthy computations repeatedly and revealing that information as well. Several cryptocurrencies have a perceived lack of privacy and ZK-SNARK implementation resolves such problems effectively.
One of the most prominent cryptocurrencies, ZCash, powered by ZK-SNARKs privacy verifies the ownership of transactions and coins more anonymously than Bitcoin and provides increased security for users.
Working of ZK-SNARK
- Setup: Initially, there’s a setup phase where a CRS or Common Reference String is generated that is used by both the prover and the verifier.
- Circuit Representation: The problem to be proven is represented as a circuit, where each gate in the circuit corresponds to a specific operation.
- Generating Proofs: The prover creates a proof by performing a series of computations on the inputs to the circuit. These computations are designed in such a way that the resulting proof convinces the verifier that the prover has correctly performed the computations without revealing any information about the inputs.
- Verification: The verifier can then check the validity of the proof against the Common Reference String. The verification process is succinct, requiring very little computational effort compared to the circuit size.
One notable downside of ZK-SNARK implementation is the need for a trusted setup phase. During this phase, the Common Reference String is generated, which could compromise the security of the system if not executed properly. However, there are efforts to mitigate this issue, such as using multiparty computation to distribute trust among multiple parties.

ZK-STARK
ZK-STARK or Zero Knowledge Scalable Transparent Argument of Knowledge is similar to ZK-SNARK, except that they offer multiple advantages such as enhanced scalability and transparency and a more robust defense against security threats while maintaining computational integrity.
Working of ZK-STARK
Here’s a simplified explanation of how ZK-STARKs work:
- Algebraic Representation: Instead of representing the problem as a circuit, ZK-STARKs represent it algebraically using polynomial equations.
- Proof Generation: The prover generates a proof by constructing a polynomial that satisfies certain properties related to the problem statement. This polynomial is constructed in such a way that its evaluation at specific points serves as evidence of the truthfulness of the statement without revealing any additional information.
- Verification: The verifier checks the validity of the proof by evaluating the polynomial at specific points and comparing the results against certain constraints.
One of the main advantages of ZK-STARKs is that they don’t require a trusted setup phase, making them more transparent and easier to deploy in practice.
Comparing ZK-SNARKs vs ZK-STARKs
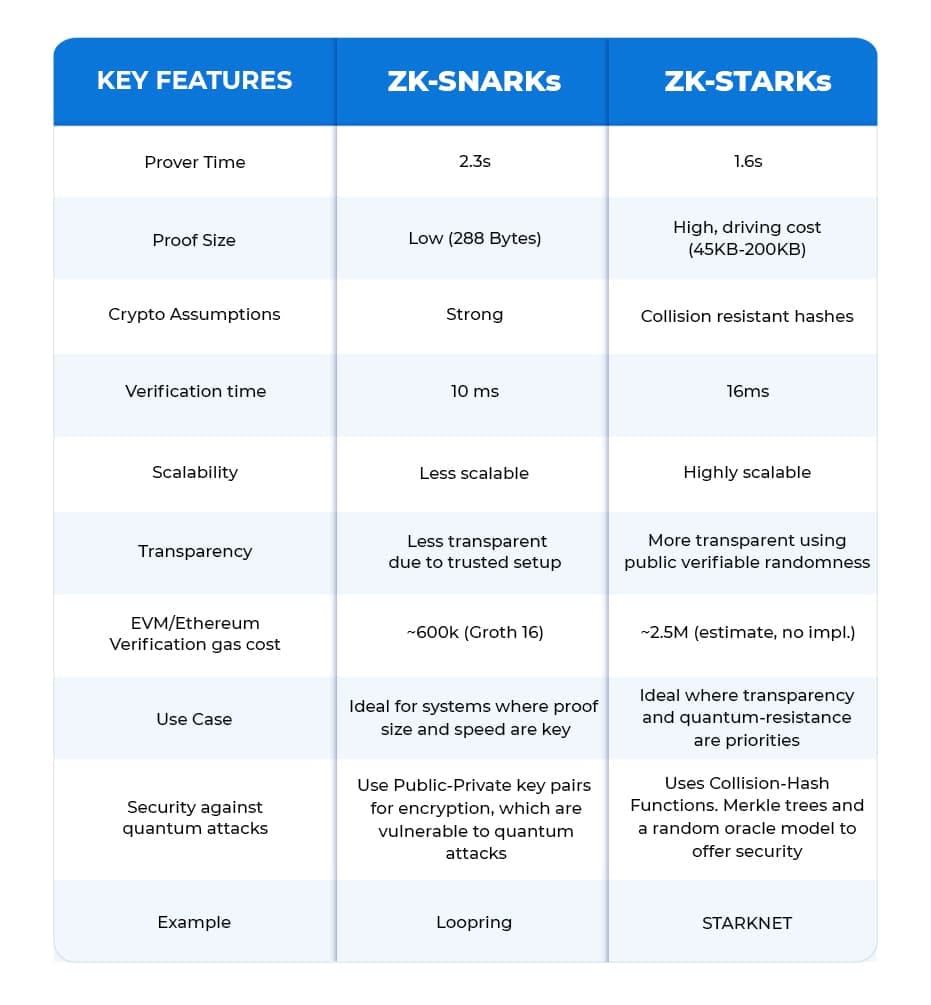
- Security
A trusted setup phase in ZK-SNARK is required that involves the development of a Common Reference String (CRS). If any malicious actors or hacktivists gain access to this setup data, they can affect the security of the system, generating false proofs. On the other hand, ZK-STARK implementation doesn’t require such a trusted setup phase, which makes it quantum-resistant & robust against security threats.
- Transparency
ZK-STARK depends on public randomness to establish parameters. It enables open and trustless verification and makes it more transparent than the trusted setup of ZK-SNARK, which relies on CRS and necessitates participants to act with honesty.
- Data Availability
ZK-SNARK is considered a more popular ZK proof, especially in layer 1 rollups for its advantage of data availability.
- Scalability
Although both cryptographic techniques offer higher scalability for blockchain, ZK-STARKS scores higher than ZK-SNARK in this aspect. ZK-STARK has a larger proof size that makes it ideal for extensive computations. It also doesn’t demand higher computational power for complex proofs, pointing to better scalability. On the other hand, the size of the ZK-SNARK proof grows proportionally when the complexity of the computations increases.
- Use Cases
ZK-SNARK implementation is popular for its consistent verification times and compact proof sizes, making it ideal for various use cases such as identity verification, privacy coins, & decentralized finance (DeFi). Meanwhile, ZK-STARKs are employed in layer 2 solutions due to their inherent transparency & scalability advantages.
Conclusion
ZK-SNARK has already been widely popular in the crypto world for its exceptional features and benefits. Z-cash is one of the cryptocurrencies that leverages the ZK-SNARK for maximum privacy and is contributing to its widespread adoption. However, concerns about the trusted setup process and potential vulnerabilities have also made way for alternatives like ZK-STARK. The ZK-SNARKs vs ZK-STARKs difference would make it easier for individuals to choose the ideal one for their project.
Overall, the development and refinement of ZK-SNARKs and ZK-STARKs represent significant advancements in the field of zero-knowledge proofs. Antier understands the future of cryptography looks promising, with privacy, security, and scalability at the forefront of innovation. Therefore, we are always ready to provide our clients with the best cryptography and layer 2 solutions development support they deserve. Connect with our team to learn more about us and our services.







