
How To Design Meme Coin IDO Launchpad Like Meme Pad In 2024?
July 19, 2024
Unlocking the Best Crypto Wallets Supporting Fiat Payments
July 19, 2024Table of Contents
- Introduction
- The Rising Need For Security In Centralized Cryptocurrency Exchange Development
- Top Centralized Cryptocurrency Exchange Development Security Features For 2024
- Top Security Measures For Centralized Exchange Development in 2024
- 3 Challenges In Secure Centralized Cryptocurrency Exchange Development
- Top 4 Centralized Exchanges Based on Security
- Conclusion
Introduction
Centralized exchanges (CEXs) are the crypto world’s friendly neighborhood portal, where a diverse cast of characters feels right at home. The unparalleled liquidity and smooth and speedy transactions fascinate experienced traders, user-friendliness amazes beginners, and the presence of central authority offers comfort to risk-averse traders. The spot trading volume on CEXs even smashed the $4.29T mark in Q1 2024, the highest since Q4 2021. This makes centralized cryptocurrency exchange development an incredible venture for anyone seeking entry into the dynamic world of digital assets.
But every rose has its thorns. CEXs, though popular among a huge trader base, have downsides. Hacks and security breaches, single point of failure risk, privacy concerns, manipulation risk, limited flexibility, and innovation often plague the user experience on CEXs. Security remains one of the most alarming concerns that must be addressed during centralized exchange development.
Dive in to learn why and how.
The Rising Need For Security In Centralized Cryptocurrency Exchange Development
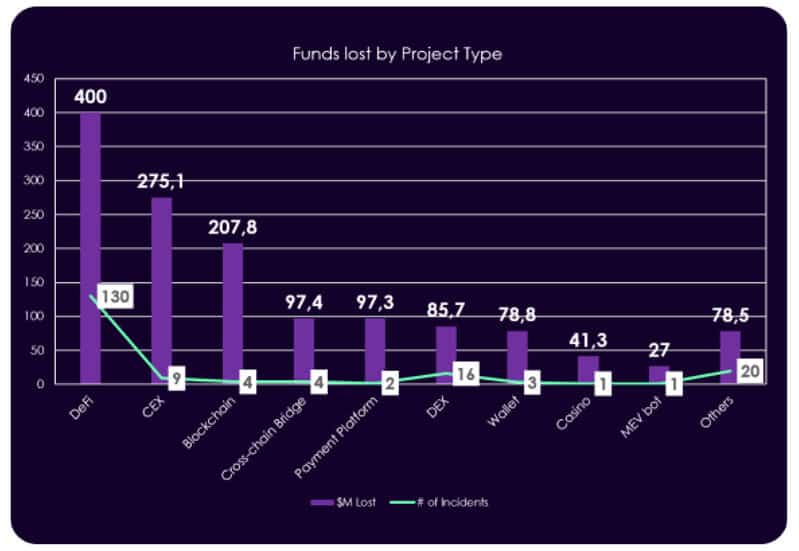
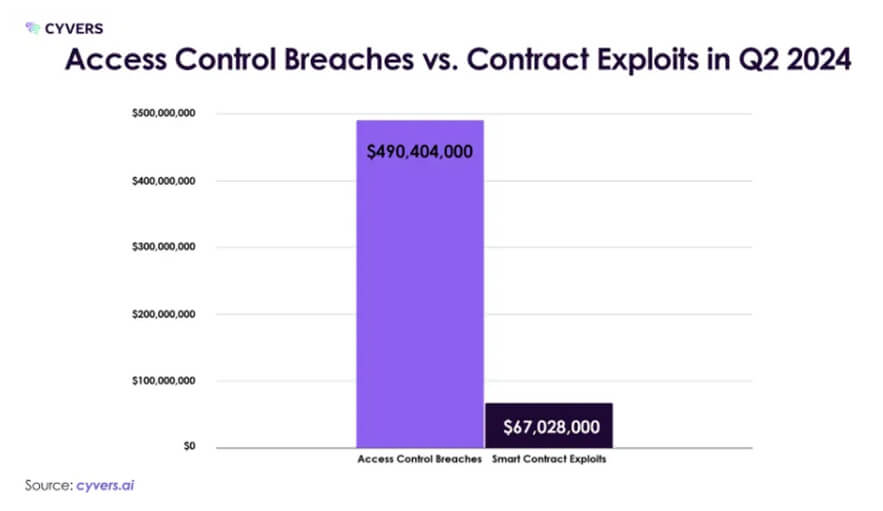
While MetaMask, Starknet, and Polygon strive to achieve mainstream adoption through new infrastructural developments, lax security standards of centralized exchanges erode the mainstream trust. The total hacked crypto funds in Q2 2024 through centralized exchanges amounted to $ 275.1 million, a 900% surge in losses compared to the previous year.
 Source: https://cyvers.ai/2024-web3-security-report-pdf
Source: https://cyvers.ai/2024-web3-security-report-pdf
The trend spotlights the concentration of crypto wealth in centralized platforms as well as security concerns overlooked during centralized exchange development. Even though there were 9 attacks on CEXs and 16 on DEXs, the CEX attacks lost more funds. The high-profile CEX attacks also fueled the need for regulatory scrutiny, leading to stringent compliance requirements and increased operational costs for exchanges. The significant fund loss is a reminder for existing centralized exchanges to hone their security measures and a lesson for new exchanges to prioritize security during centralized cryptocurrency exchange development. Another potential reasons why CEXs need to tighten up their security may include:
- Growing profit margins: The growing value of digital assets also increases the incentive for attackers to target these exchanges.
- Concentration of funds: Due to high transaction volumes, CEXs hold substantial amounts of funds. Since CEXs have control over users’ funds, they become frequent targets for hacks and breaches.
- Regulatory Scrutiny: Regulatory bodies are increasingly emphasizing cybersecurity for exchanges so prioritizing security during centralized exchange development is essential to dodge the regulatory watch.
- Increased Attack Sophistication: Cybercriminals are constantly developing new and sophisticated attack methods
- User Trust and Security: Users often become wary of their funds and sensitive information security after attacks. Therefore, security breaches can greatly tarnish a brand’s reputation and revoke users’ trust in a trading platform.
Implementing robust security measures during centralized cryptocurrency exchange development helps businesses stay compliant and ahead of the curve. The next section mentions top security features that can help exchanges safeguard against potential threats.
Also Read>>> 7 Reasons Centralized Cryptocurrency Exchange Development Is Profitable in 2024
Top Centralized Cryptocurrency Exchange Development Security Features For 2024
Without much ado, have a look at a list of the top centralized cryptocurrency exchange development security features:
- Secure Password Hashing & Email Verification:
- Advanced Encryption Techniques
- Multi-Factor Authentication (MFA)
- Session Management
- Address Whitelisting
- Secure Network Infrastructure
- Cold Wallet Storage
- Secure API Access
- Multi-Signature Wallets
- DDoS Protection
- Biometric Authentication
- Regulatory Compliance and Auditing
- Anti-Money Laundering (AML) and Know Your Customer (KYC) Procedures
- Real-Time Monitoring and Incident Response

Also, Read>>> Top 8 Centralized Crypto Exchange Development Trends in 2024
Top Security Measures For Centralized Exchange Development in 2024
Centralized exchanges are certainly honeypots. As more money gets poured into the CEXs, they become relatively larger honey pots, and they will remain enticing prey for malicious actors out there. But what if there were ways to keep the parasites away? Well, there are so many of them. By partnering with a Centralized Exchange Development Company, you can hold huge funds and still keep malicious minds at bay. Let’s discover some of those you can leverage to address emerging threats and vulnerabilities in the Web3 space.
Overcoming Cybersecurity Threats In CEXs: Top 5 Practices
The largest attacks in the history of centralized exchange platforms involve DDoS attacks, phishing, ransomware, or social engineering attacks. Combating these risks requires implementing sophisticated cybersecurity measures during centralized cryptocurrency exchange development.
- Multi-factor Authentication (MFA): MFA adds to security by requiring additional verification factors beyond mere passwords, such as biometric authentication (fingerprint, facial recognition). This adds to the security, as even if hackers crack the first factor, they’ll need to smash another to access users’ accounts/funds. Stringent user verification and authentication measures integrated during centralized exchange development ensure that only authorized users securely deposit and withdraw funds, bolstering account security, and defending against breaches.
- Monitoring and Threat Detection: Firewalls and Intrusion Detection Systems (IDS) minimize the chances of unauthorized intrusion and monitor malicious activities in trading environments. AI-based IDS can potentially enhance the system’s resistance to unauthorized access. Additionally, your centralized exchange development company may suggest different protocols to proactively identify and address potential threats using real-time transaction monitoring, anomaly detection systems, and Security Information and Event Management (SIEM).
- Network Security and Infrastructure: Implement robust measures like DDoS protection, network segmentation, and secure coding practices to safeguard your exchange’s infrastructure and minimize the risk of introducing vulnerabilities through coding errors. Another challenge may arise while scaling the infrastructure to accommodate the exchange’s growth. A reliable centralized exchange development company will introduce complex software and hardware solutions to increase scalability only after thorough testing and code audits. Leveraging robust security protocols that scale efficiently, such as multilayered security mechanisms, is a recommended practice.
- Advanced Encryption Mechanisms: Encryption involves converting the susceptible data into a secure format that can only be accessed or processed after being decrypted. The encryption technique leveraged during centralized exchange development can be symmetric or asymmetric. The prior encryption technique uses the same key for both encryption and decryption, making the process faster but less secure. Asymmetric encryption uses separate keys for both, adversely affecting speed but enhancing security. Choosing the right encryption mechanism during centralized exchange development is essential to safeguarding sensitive data.

- Bug Bounty Programs, Regular Security Audits, and Penetration Testing: Last but not least, it is always better to find those vulnerabilities before a hacker finds them and disrupts the user experience. One of the most commonly used measures to achieve this is by hosting bug bounty programs, in which exchanges incentivize white hat hackers to find and report vulnerabilities before malicious actors exploit them. Additionally, exchanges must engage their partner centralized exchange development company and top security firms in regular penetration testing and security audits. Regular penetration testing helps them identify and address susceptibilities in exchange infrastructure at the earliest. Comprehensive security audits involve evaluating the system’s physical environment and configuration, information handling, software, and user practices for security. The exchanges must join forces with their centralized exchange development company to maintain their security protocols and ensure ongoing security in the face of emerging threats.

3 Challenges In Secure Centralized Cryptocurrency Exchange Development
1. Opaque Systems Obscuring Funds Allocation & Handling Information
In CEXs, a centralized third party aggregates the user funds into exchange-owned digital custody solutions (or hot wallets) to create a liquidity pool to facilitate seamless transactions. After making funds available to trade through hot wallets, the CEXs are expected to offload the rest of the funds to “cold storage” or offline custody solutions. This is industry-standard practice but exchanges usually prefer to keep the information about owning and handling the transactions under wraps, making them a shady figure in the world of finance.

Solution: Following industry standards and enhancing transparency is the key to staying trusted. Exchanges like Coinbase are public companies that set industry standards high and remain an open book so customers can trust them. Any new centralized exchange development project must consider such a policy and clearly state to users how they are handling their funds and earning from the business.
2. Navigating the Complex Regulatory Maze:
Not all exchanges enter the space to earn legitimately; however, it is usually difficult to detect. An exchange might not reveal this monopolistic and corrupt side in the beginning but may slowly start to engage in wash trading (a practice that involves the exchange creating bogus volume), insider trading, and crypto price manipulation. They may charge higher fees and impose withdrawal limits suddenly. Regulations are therefore a necessary component of centralized exchange development. But for the past few years, the regulatory environment around exchanges has been evolving rapidly and it has recently become stern for even the legitimate businesses in the CEX space.
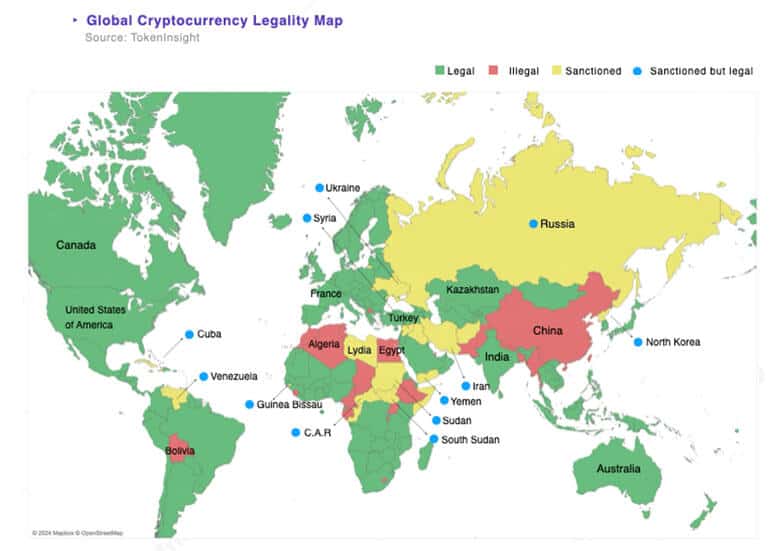
Source: TokenInsight
Solution: Stay updated on evolving regulations related to cybersecurity and AML/KYC compliance for crypto exchanges. Legitimacy is equally important to maintain users’ trust in an exchange platform. You can read this blog to learn more about the compliance and licensing requirements for centralized cryptocurrency exchange development.
3. Insider Risks
These types of risks come from individuals within the organization who misuse their access to sensitive systems and information for their own selfish interests or to tarnish the exchange’s reputation. These are some of the most severe and hard-to-detect threats, as they come from a legitimate source. The motivation behind such risks may be anything ranging from personal grievances to financial gains but the effect is certainly tumultuous as they can cause heavy financial losses and majorly erode users’ trust in a CEX.

Solution: Partnering with a centralized exchange development company to integrate strict access controls and monitoring systems can help exchanges combat the risk of insider defaults. Implementing stringent physical infrastructure security and surveillance systems can also slash the chances of such frauds, as malicious minds can then fear the risks of being tracked. Besides, exchanges can consider optimizing ethical corporate culture.
Also Read>>> Top 5 Centralized Exchange Development Companies in 2024
Top 4 Centralized Exchanges Based on Security
It’s important to note that maintaining security is not a one-time process that is required at the time of centralized cryptocurrency exchange development. It is an ongoing process, and no exchange is completely immune to attack. However, the following are some CEXs that have consistently demonstrated a strong commitment to security:
1. Bitget
- First renowned exchange for having a zero hack security record and a spotless track record, ensuring fund and data safety.
- Highly transparent exchange activity and proof-of-reserve data.
- Keeps a customer protection fund of $300 million
2. Coinbase
- A user-friendly centralized exchange development project that evolved its security systems after experiencing brutal hacks in the past.
- Fewer security hacks faced compared to other competitors.
- A lawful public entity ensuring high financial transparency.
- Regularly audited by independent third parties (as a regulatory measure).
3. Kraken
- Renowned for a premium pack of security features and advanced trading features, including margin trading, NFTs, and futures.
- A professional exchange best suited for experienced digital asset traders
- Affordable transaction fees
4. Binance
- One of the largest CEXs globally, it employs advanced security protocols, including AI-based fraud detection.
- Multi-layered security architecture and a huge team of security experts.
- Invests heavily in centralized exchange development security measures.
Conclusion
Security is no longer an afterthought; it’s a fundamental requirement for any successful CEX in 2024. By implementing the security features and measures outlined above, centralized exchanges can create a more secure and trustworthy environment for their users and the entire cryptocurrency ecosystem.
Interested in strengthening the security of your existing centralized exchange or your new centralized cryptocurrency exchange development project? Hire Antier, and we’ll take care of everything so that you can rest assured that your project is in safe hands. We have experience implementing cutting-edge security features for our clients. So, what are you waiting for?
Get in touch with us today and let’s secure the future of your centralized exchange.



