Build DePIN Infrastructure That Drives Tomorrow’s Economy
Enable transformative growth through decentralized physical infrastructure networks. Leverage advanced blockchain architecture to create scalable, secure, and energy-efficient solutions that redefine how industries operate and interact.
Get Started
Unleash Multi-Chain Potential with Cutting-Edge Chain Abstraction
Accelerate your blockchain strategy with seamless interoperability across networks. Our chain abstraction solutions simplify complex ecosystems, enabling rapid communication between multiple chains. Optimize performance, ensure scalability, and future-proof your operations with flexible, decentralized applications.
Get Started
Build DePIN Infrastructure That Drives Tomorrow’s Economy
Enable transformative growth through decentralized physical infrastructure networks. Leverage advanced blockchain architecture to create scalable, secure, and energy-efficient solutions that redefine how industries operate and interact.
Get Started
Unleash Multi-Chain Potential with Cutting-Edge Chain Abstraction
Accelerate your blockchain strategy with seamless interoperability across networks. Our chain abstraction solutions simplify complex ecosystems, enabling rapid communication between multiple chains. Optimize performance, ensure scalability, and future-proof your operations with flexible, decentralized applications.
Get Started
Build DePIN Infrastructure That Drives Tomorrow’s Economy
Enable transformative growth through decentralized physical infrastructure networks. Leverage advanced blockchain architecture to create scalable, secure, and energy-efficient solutions that redefine how industries operate and interact.
Get Started
Unleash Multi-Chain Potential with Cutting-Edge Chain Abstraction
Accelerate your blockchain strategy with seamless interoperability across networks. Our chain abstraction solutions simplify complex ecosystems, enabling rapid communication between multiple chains. Optimize performance, ensure scalability, and future-proof your operations with flexible, decentralized applications.
Get Started
Crafting Non Fungible Excellence
Delivering Web3 Strategic Objectives

BLOCKCHAIN
Antier delivers breakthrough blockchain solutions to shape the next generation of enterprises move smarter and faster than ever.

Metaverse
We create the critical mass needed to help organizations mark their breakthrough moments in new virtual environments.

Finance Solutions
Through the lens of our extensive industry expertise, we offer a customized suite of capabilities designed to address your specific use cases.

Artificial intelligence
We activate next-generation autonomous algorithms and generate highly actionable predictions to achieve true north for your business

Driving Ingenuity with Relentless Blockchain Innovation

Harmony

Tezos
ZetaChain

Hyperledger
Fabric

Cardano

ICP

Ton

Klaytn

Telos

Ripple
Boba Network
Pirichain

Ethereum

Polygon

Binance

Solana
Skale
Tron
Avalanche

Polkadot

Cosmos

NEAR
Protocol

Corda

Harmony

Tezos
ZetaChain

Hyperledger
Fabric

Cardano

ICP

Ton

Klaytn

Telos

Ripple
Boba Network
Pirichain

Ethereum

Polygon

Binance

Solana
Skale
Tron
Avalanche

Polkadot

Cosmos

NEAR
Protocol

Corda

Harmony
Ethereum

Polygon

Binance

Solana
Skale
Tron
Avalanche

Polkadot

Cosmos

NEAR
Protocol

Corda

Harmony

Tezos
ZetaChain

Hyperledger
Fabric

Cardano

ICP

Ton

Klaytn

Telos

Ripple
Boba
Network
Pirichain
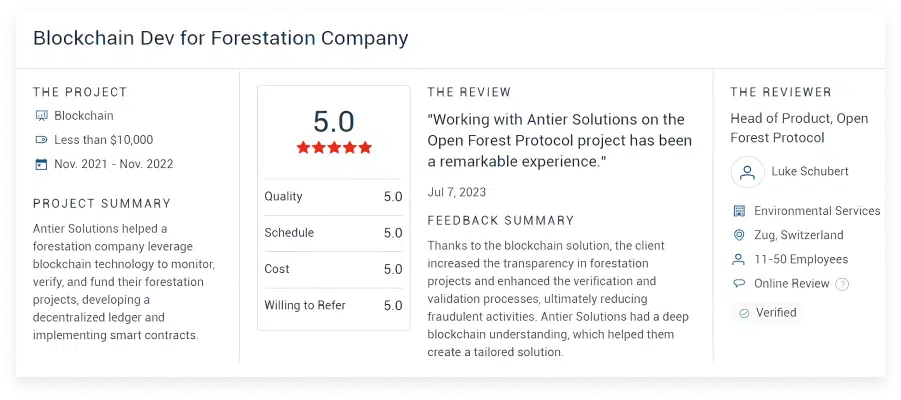
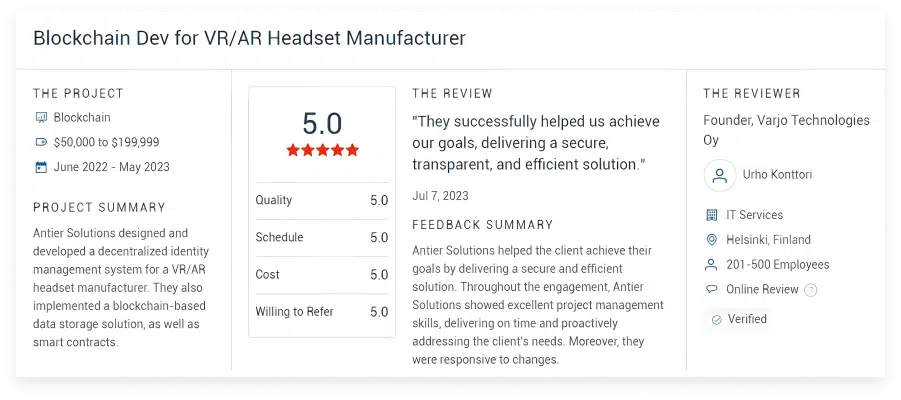
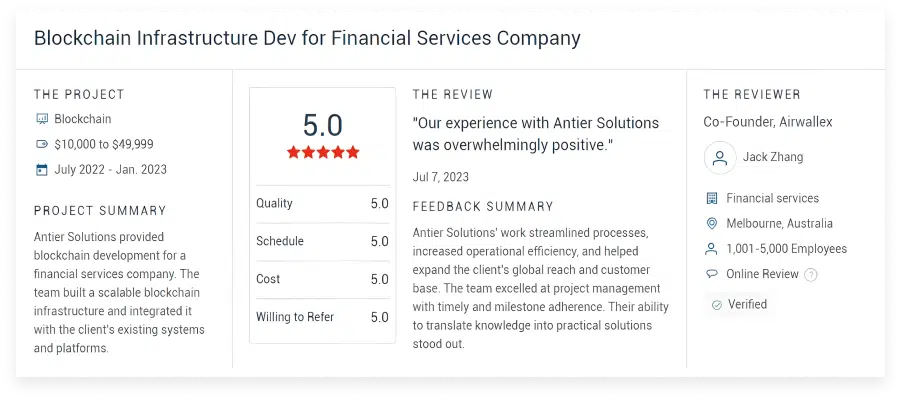
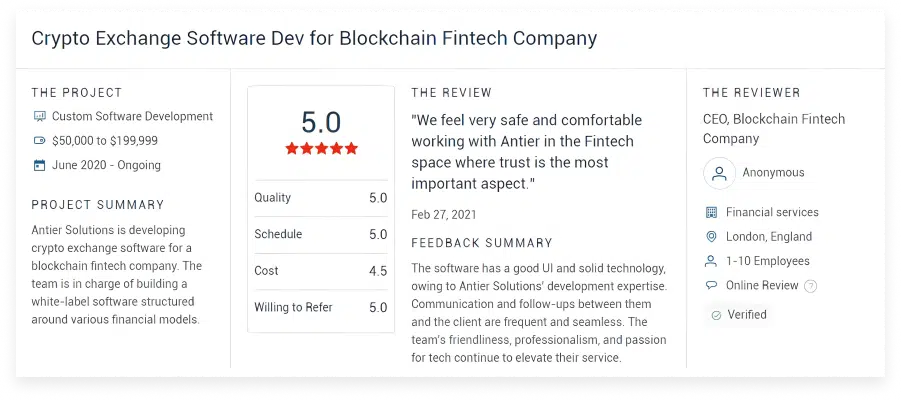
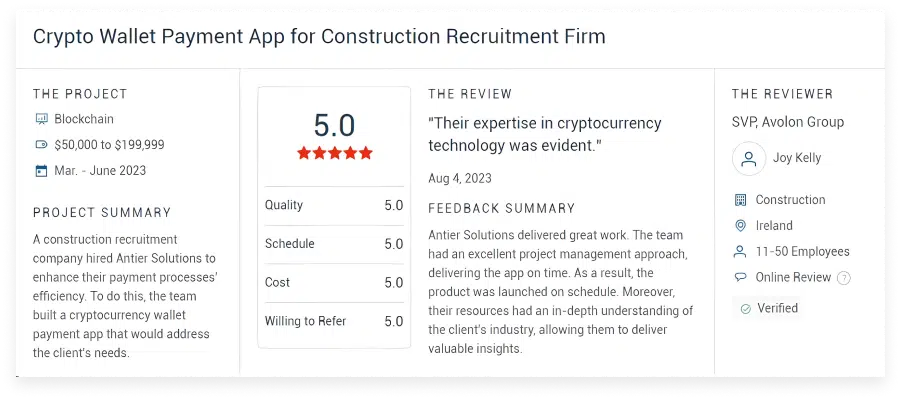
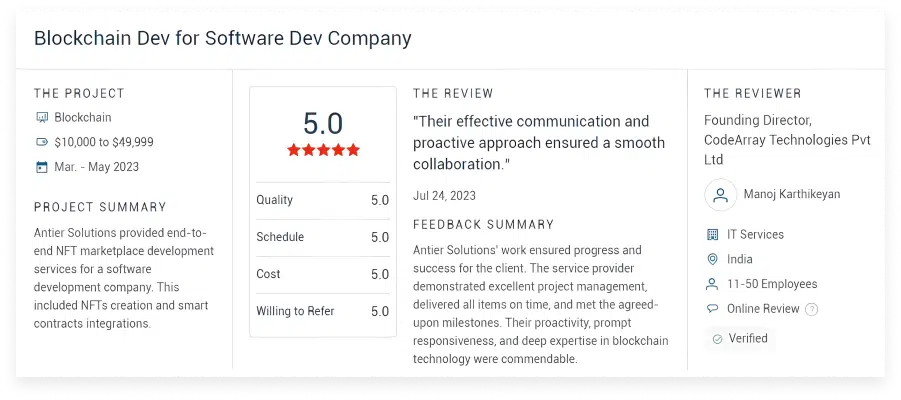
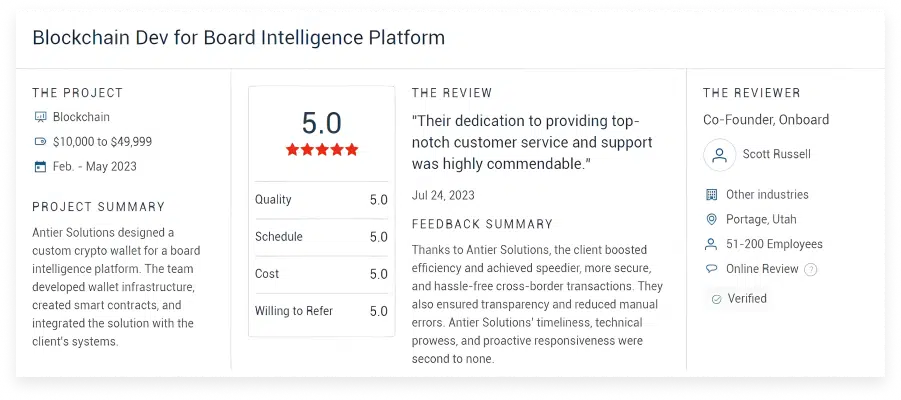
What Clients Say